Veracrypt with PIM | Extra Security Added
Encrypting your sensitive data is important. As you may know, CIA...
- Confidentiality
- Integrity
- Availability
...are the essential elements of Information Security.
There are a number of tools and methods available out there, but not all encryption tools are same.
VeraCrypt, a TrueCrypt alternative, is an open source file encryption software designed to protect your online privacy.
VeraCrypt enters the market within months after TrueCrypt died, almost similar to it, but with enhancements to further secure your data.
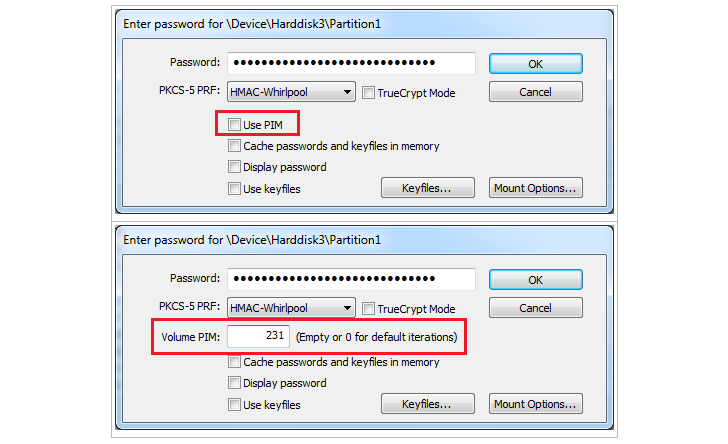
A week ago, latest version VeraCrypt 1.12 released with a new feature called PIM, which stands for "Personal Iterations Multiplier".PIM (Personal Iterations Multiplier) is a new parameter introduced in VeraCrypt 1.12 to secure your data.
Your Password is being used to mount the encrypted container or partition, whereas…
PIM value will decide the number of iterations, or in simple term, the speed of the mounting and booting process, simply brilliant. This feature makes the software a minimum of 10 and a maximum of nearly 300 times harder to brute force.
Download it from the Veracrypt 1.12 Home Page.
#veracrypt#encryptypyourdisk#PIM#moreaddedsecurity#hardtobypass 

Comments
Post a Comment